- HubPages»
- Technology»
- Internet & the Web»
- Viruses, Spyware & Internet Security
System Security Virus: Malware Prevention and Removal
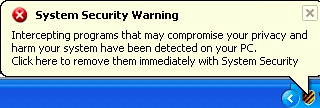
What's peculiar about system security virus?
Compared to an array of rogue security programs circulating on the web, system security virus is particularly annoying. It's stubborn. It makes Windows unusable. Owners of infected machines would scream in despair. Help on forums? Unsuspicious users will enumarate a dozen of recovery steps that do work, but not with system security.
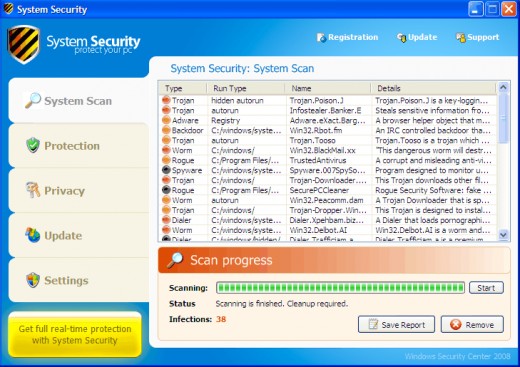
The Bad
Once this malware is inside your PC, it causes chaos.
- Your installed antivirus or antispyware program is likely to miss the infection. If real-time protection fails, you will not be able to open antivirus control panel or initiate a scan.
- For testing purposes, I'm running PC Tools Internet Security. Mind you, this application is useless. It lists suspicious activity in the History section, and even blocks access attempts, but it can neither detect nor remove parts of malware.
- System Security virus can block: Registry Editor (regedit.exe or regedt32exe), Task Manager (taskmgr.exe), Command Prompt (cmd.exe).
- Installation of new programs will fail meaning you just can't install any security software to remove this virus.
- Online virus scanners will not run due to various errors. A victim of System Security reported that she was able to use a-squared anti-malware scan though.
a-squared Web Malware Scanner
- Anti-malware Online Check
Use Internet Explorer to scan your system. There's no guarantee though that a computer infected with System Security will be capable of running this check. Web Scanner needs to download about 17 MB of data, so this is for high-speed connections only.
Inside the Infected Computer
- "Security System Firewall Alert" is continually popping up on your PC when you're on the Internet.
- This malware generates a random numeric filename, e.g. C:\Documents and Settings\All Users\Application Data\2068231618\491559532.exe
- It installs its files into C:\Program Files\System Security.
- To autostart with Windows, System security 2009 virus adds entries to the Registry. However, this pest is smart enough to prevent attempts of modifying the Windows registry hive, so deleting malicious keys manually may come impossible.
Entry Point: Email
This is an email I got into my inbox:
Hello Kelly,
I found your information while trying to research a way to remove the System Security Malware program. I have a decent amount of experience with getting rid of this types of fake anti virus programs, but this one has me completely stumped. I am locked out of Task Manager, regedit, i can't open any .exe file and i can't get into safe mode. I was just wondering how you ended up getting it off of your computer, if you did at all. I can't install Malwarebytes because it won't let me open the exe file. The only program i can open is internet explorer. I tried renaming the malwarebytes install file to "iexplorer.exe" and opening it, but that still didn't work.
Any information you can pass on my way would be greatly appreciated.
Thank you in advance,
Josh.
Look how innocent it is. I'm getting emails asking for help daily, so this one was no surprise. But I wasn't yet finished with the reply when another one arrived:
Hello again,
I found the solution. Just in case you have not, http://systemsecuritysite.com/install/wscleaner.exe , it was supplied by the website in the support page. That kills the process and allows you to open the exe files. I now can run malware bytes and can completely remove the program from my system.
-
Josh
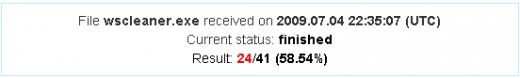
This one explained it all. Chances are, a poor victim suffering from the malware and searching for ways how to remove system security virus, will receive this 'request for help' followed by a 'quick cure' with the link. Downloading and executing the file is not recommended, because as you might have already guessed, it's another piece of malware. Virustotal reported it malicious after scanning the item with 41 different antivirus engines.
How to Remove System Security
Basically, in case Registry Editor, Command Prompt and Task Manager are blocked by malware, the only way out is to use Windows Safe Mode because you can't install any removal software in Normal Mode.
Here's System Security removal procedure using Safe Mode.
- Restart and keep tapping F8 key until Windows Boot Menu appears. Choose Safe Mode with Networking (or just Safe Mode).
- Log on with administrator privileges.
- Open Task manager, locate the process consisting of random numbers (e.g. 1213501838.exe), highlight it and click End Process. Repeat this with SystemSecurity.exe process if listed.
- Open Microsoft Configuration Utility (Start-->Run, type in MSCONFIG and click OK. Navigate to Startup tab). Look for entries pointing to 1213501838.exe and SystemSecurity.exe (these are examples only, the filename with numbers is randomly generated by malware), uncheck their corresponding boxes. Click Apply, OK.
- Restart Windows and log on normally.
Recovering
When logged on, you should be no longer seeing pop-ups and warnings. However, the steps you did in Safe Mode are not meant to remove system security. For complete removal, download and install any of the programs below. There's no need to install all of them, just pick up 1 and do a system scan with it.
Malwarebyte's
- Malwarebyte's Anti-malware
This tiny application with minimalistic interface is #1 malware destroyer. If due to System Security virus intervention no download is possible, read the tip on the left.
Tip for Malwarebyte's users
Chances are, it won't let you neither download nor install Malwarebyte's anti-malware. If this is the case, change the filename mbam-setup.exe to explorer.exe (this might fool our smart little pest). Save explorer.exe to your hard drive, and execute. If Malwarebyte's installs, good. Now go to C:\Program Files\Malwarebyte's Anti-malware and rename mbam.exe to explorer.exe. Try running the renamed file. When Malwarebyte's window open, go to Update tab and download latest updates, then perform a scan.
SUPERAntiSpyware
- SUPERAntiSpyware v4
SUPERAntiSpyware Professional - lightweight, unobtrusive application with rock-solid protection against malware.
Post-recovery
Since System Security virus places its files into System Volume Information (a hidden Windows folder), you need to empty it.
WARNING 1: do this only after the program you picked up above, completed a successful scan and removed parts of the malware. System Volume Information is a protected folder so security software might be unable to delete System virus from there.
WARNING 2: make sure your system is operating normally, i.e. all applications can be opened, you have access to Task Manager and Add/Remove Programs applet, etc. There should be no more malware (except for System Volume Information where remnants of the virus might be remaining).
- Right-click on My Computer and choose Properties.
- Go to System Restore.
- Check the box Turn off System Restore. Click Apply, OK. Windows will warn you about the danger of deleting restore points. After restarting Windows, reverse the steps, that is, Enable System Restore.
Prevention
Finally, a couple of words about protection.
If you ever had a chance to tackle any rogue security program (not necessarily System Security pest), you definitely know how tedious, time-consuming and exhausting the task can be.
Therefore take this piece of advice from me:
- Consider switching your current security software, namely antivirus. It doesn't matter if you're using a multi-module Internet Security Suite from any vendor. Once the malware has been let into the system, it will come back. The story will repeat. So if you don't learn the lesson and leave everything as it is, I'm sorry you wasted your valuable time reading this hub.
- Revise your browsing habits. If you're using Google, pay attention to warnings it gives under listings of suspicious websites. If Google thinks a website is dangerous, chances are there's a reason behind that warning.
- Remind yourself and instruct anyone sharing your computer: DO NOT install any antivirus, antispyware, security scanner, etc, no matter where and what is recommended. Once your layers of protection are set up and functioning, stop experimenting and ignore flashy warnings like "your system is infected, take action!"








